
A user known as “maxlin.eth” on platform X encountered a job-hunting scam where attackers conducted a Zoom call to deceive a potential victim into downloading a malicious app.
A fake video conferencing software is being used for address-poisoning attacks aimed at stealing crypto assets from community members.
SlowMist founder Yu Xian shared a report from a community member, urging everyone to be cautious and avoid using unfamiliar software for video conferencing. According to Xian, these fake programs are designed to steal digital assets.
X User Shares Job-Hunting Scam Experience
An X user, “maxlin.eth,” reported experiencing a job-hunting scam. The user recounted that a scammer, posing as a human resources representative from the infrastructure development firm xLabs, contacted them via Telegram.
The scammer claimed to have reviewed the user’s Web3 career and offered a marketing specialist position. Due to xLabs’ reputable status, the user initially believed the offer might be genuine.
The scammer avoided typical tactics such as sending direct links to malicious software. Instead, they conducted a fake job interview over Zoom with a different individual, creating an illusion of legitimacy.
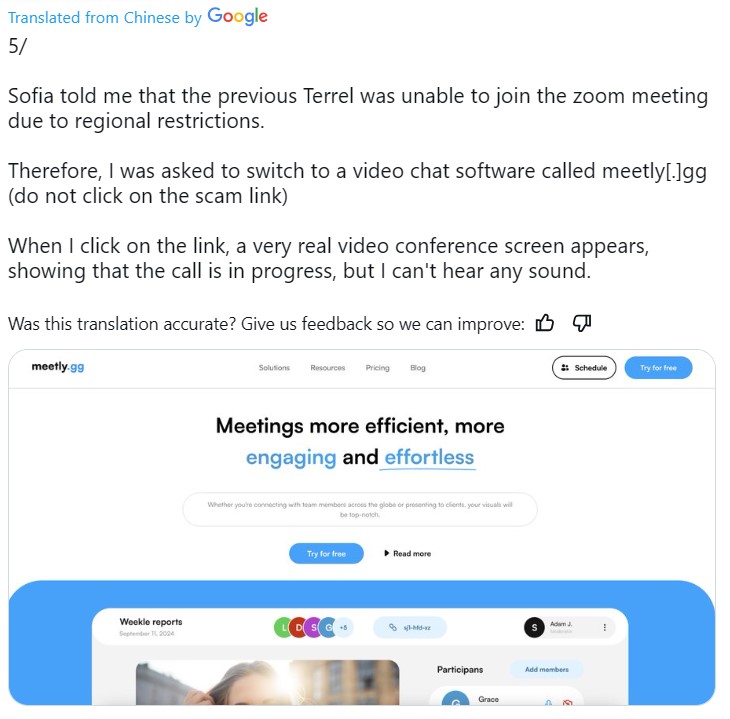
During a half-hour conversation about xLabs’ vision and products, the scammers lowered the victim’s guard. They then requested the user switch to a different meeting software, as the initial contact could not join via Zoom.
The user was instructed to download a software called Meetly. Upon clicking the link, the user encountered a seemingly real conference screen but no sound. The scammers insisted on downloading the software onto the user’s computer. After installation, the application kept freezing, and the session ended.
Subsequent research revealed that the link shared by the scammers was widely reported as fraudulent. Additionally, the user found no xLabs employees with the names provided by the scammers and discovered that xLabs had no marketing specialist openings.
Realizing the scam, the crypto user transferred their assets to different wallets, preventing potential theft.
Similar Strategies Used in MonoSwap Hack
Hackers employed a similar strategy in the breach of the decentralized exchange (DEX) and staking platform MonoSwap. On July 23, one of the platform’s developers was lured into a call by scammers posing as venture capitalists. During the call, malicious software was installed on the developer’s computer, which had access to the DEX’s wallets and contracts. This allowed the hackers to withdraw staked liquidity from the exchange.
Conclusion
The incidents underscore the importance of vigilance in the crypto community. Users should be wary of unfamiliar software and verify the legitimacy of job offers and contacts to protect their digital assets.
Source: Cointelegraph

Comments