
A new and sophisticated scam involving a malicious Zoom look-alike is tricking users into installing malware. This scam deceives users by making it seem like a video conference is stuck loading, prompting them to install even better-disguised malware than before.
Crypto scammers are once again causing trouble, using malicious links to a webpage that closely mimics the video conferencing platform Zoom. When users click on these links, they are prompted to install malware.
On July 22, non-fungible token (NFT) collector and cybersecurity engineer “NFT_Dreww” warned X users about an “extremely sophisticated” crypto scam involving fake Zoom links.
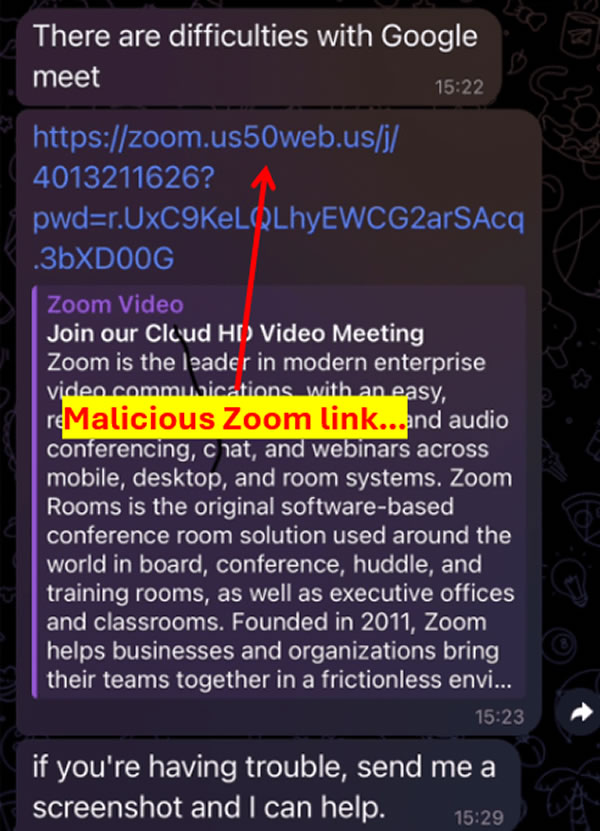
Malicious Zoom link. Source: NFT_Dreww
How the Scam Works
Dreww explained that scammers often target NFT holders or crypto enthusiasts, pretending to be interested in licensing intellectual property, inviting them to Twitter Spaces, or asking them to join a new project team.
The scammers insist on using Zoom and pressure the target to join a meeting using a subtle malicious link.
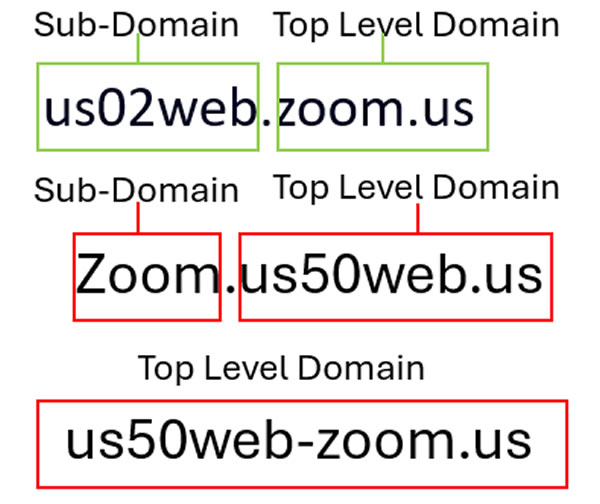
Comparing the malicious domain with the genuine one. Source: NFT_Dreww
“It’s extremely easy to fall for this… I doubt 80% of people verify each character in a link that’s sent, especially a Zoom link.”
When the link is clicked, the user encounters a “stuck” page with an infinite loading screen. This page then prompts the user to download and install ZoomInstallerFull.exe, which is actually malware.
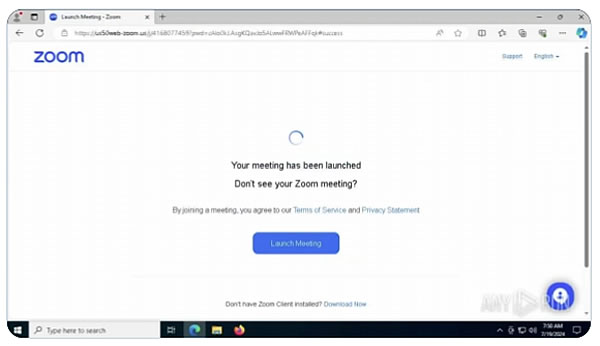
Screenshot of malware being installed. Source: any.run
Once installed, the page redirects to the official Zoom platform, making the user believe it worked. By this point, the malware has already infiltrated the target computer and stolen data and assets.
According to technologist “Cipher0091,” who Dreww credits for his X thread, the malware adds itself to the Windows Defender exclusion list to evade antivirus systems. It then extracts information while distracting the user with the “spinning loading page” and the process of accepting terms and conditions.
Dreww added that scammers frequently change domain names to avoid detection, and this is their fifth domain for this scam.
Ongoing Threats
Social engineering crypto scams are not new, but they continually evolve. Several crypto community members have reported receiving malicious emails this week from scammers impersonating other crypto influencers and executives.
These emails contain malicious attachments that, if executed, likely install crypto-stealing malware.
Source: Cointelegraph

Comments